HIPAA Compliant Software
Discover Carepatron, the ultimate HIPAA-compliant software for healthcare pros. Secure, efficient, & patient-centered—your ideal digital health partner.


What is a Type 2 Diabetes Diet Food List?
Navigating the dietary needs of patients with Type 2 Diabetes can often feel like walking through a maze without a map. That's where the Type 2 Diabetes Diet Food List comes into play, offering a clear, structured path for healthcare professionals and their patients.
This comprehensive list is more than just a collection of foods; it's a tailored guide designed to help manage blood sugar levels effectively. It categorizes foods based on their nutritional value, glycemic index, and overall impact on blood sugar control. Each category, from fruits and vegetables to grains and proteins, is carefully curated to provide healthy and satisfying options.
But why is this list so crucial? For individuals with Type 2 Diabetes, every meal choice can significantly impact their blood sugar levels, overall health, and well-being. The Type 2 Diabetes Diet Food List is vital in educating patients about the foods that support their health goals. It empowers them to make informed decisions about their diet, ensuring they can enjoy a variety of foods while keeping their diabetes in check.
This list is valuable for healthcare professionals in dietary planning and patient education. It simplifies the complex task of dietary management in diabetes care, providing a clear framework to work within. By integrating this list into patient care plans, healthcare providers can offer more personalized, practical dietary advice, helping patients navigate their dietary choices confidently and efficiently.
In essence, the Type 2 Diabetes Diet Food List is not just about listing safe foods; it's about fostering a healthier, more informed approach to eating for diabetes management. It's a testament to the power of nutrition in transforming health outcomes, making it an indispensable tool in the arsenal of healthcare professionals.
HIPAA Compliant Software Template
HIPAA Compliant Software Example
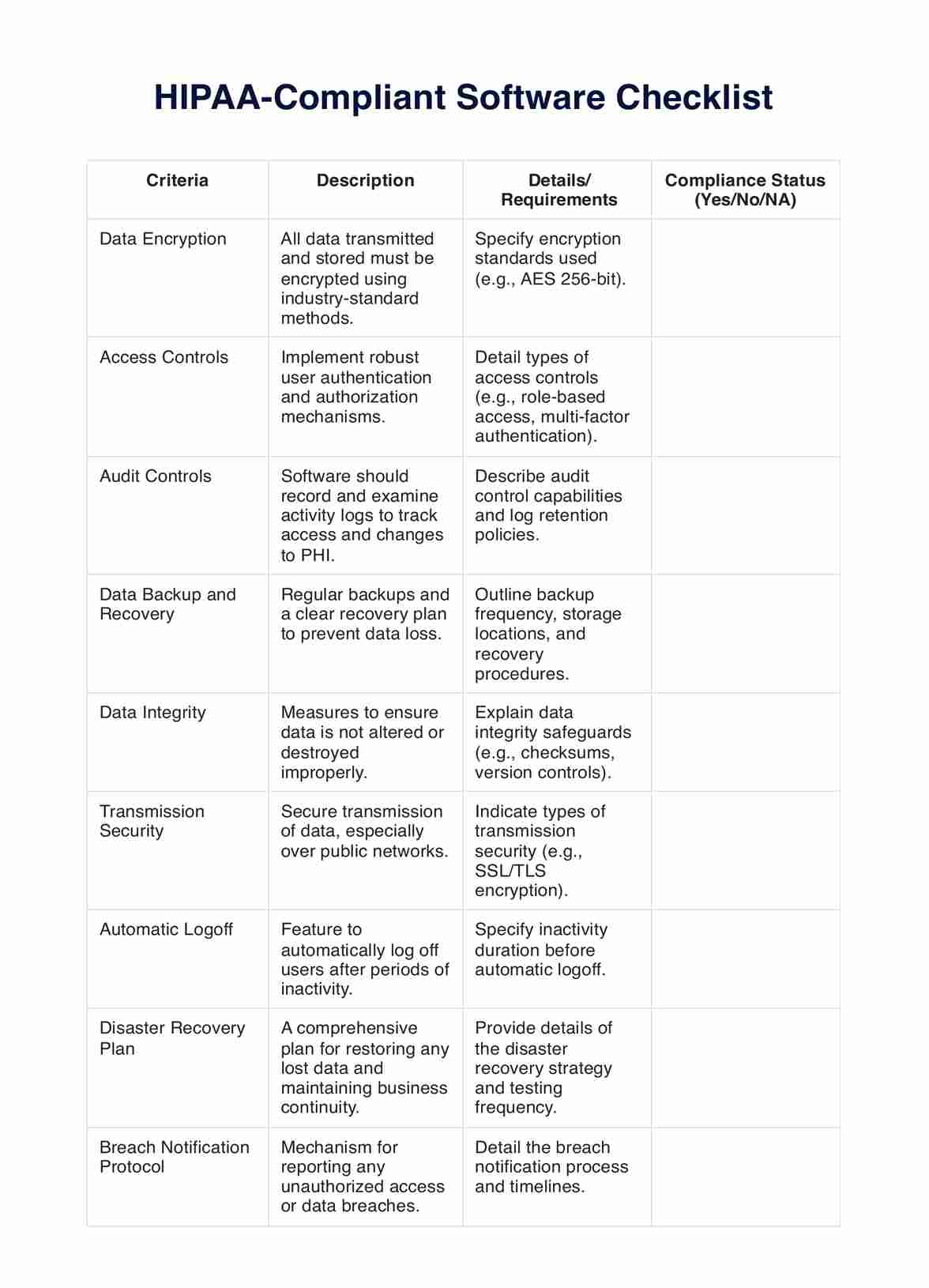
How to use the HIPAA-Compliant Software Checklist
Understanding and implementing the HIPAA-Compliant Software Checklist is crucial for healthcare professionals to protect patient information. This checklist serves as a comprehensive guide to evaluate and maintain the compliance of software systems with HIPAA regulations.
Introduce the Checklist
Begin by introducing the HIPAA-Compliant Software Checklist to your team. Explain its importance in safeguarding patient data and ensuring legal compliance. Highlight how each criterion on the checklist contributes to the overall security and privacy of patient health information (PHI).
Conduct Training Sessions
Organize training sessions for staff to familiarize them with HIPAA requirements and the specific elements of the checklist. Ensure that everyone understands the purpose and importance of each criterion, including data encryption, access controls, and breach notification protocols.
Regularly Review and Update the Checklist
Regularly review the checklist to ensure it remains current with evolving HIPAA regulations and technological advancements. Update the checklist as necessary and communicate these updates to all relevant staff members.
Implement the Checklist in Software Assessments
Use the checklist when assessing, selecting, and implementing any new software in your healthcare practice. Ensure that all software meets the criteria outlined in the checklist before it is used to handle PHI.
Document Compliance
For each software system used, document compliance against the checklist criteria. Keep records of these assessments for accountability and reference during audits or inspections.
Address Non-Compliance Issues
If any non-compliance issues are identified, take immediate steps to address them. This may involve software updates, additional staff training, or changes in operational procedures.
The HIPAA-Compliant Software Checklist is a vital tool for maintaining the integrity and security of patient data. Regular use and adherence to this checklist will ensure that your healthcare practice remains compliant with HIPAA regulations, protecting your patients and your practice.
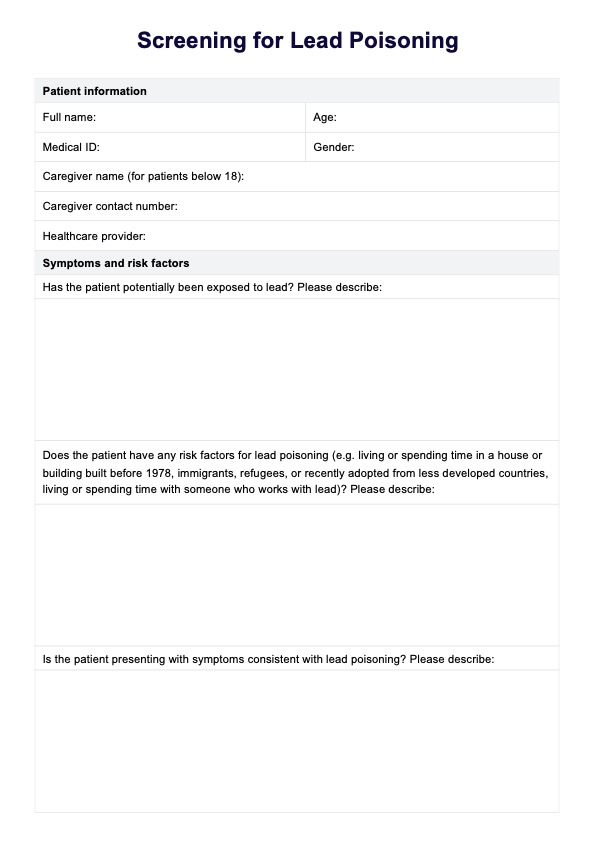
When Would You Use This Form?
The HIPAA-Compliant Software Checklist is essential for healthcare professionals, ensuring that the software they use adheres to HIPAA's stringent privacy and security standards. Knowing when to utilize this form is crucial for maintaining compliance and safeguarding patient information.
During Software Evaluation and Selection
Before integrating any new software into your healthcare practice, use the checklist to evaluate its compliance with HIPAA regulations. This ensures that patient data will be handled securely and according to legal requirements.
Annual Compliance Audits
Regularly scheduled compliance audits are a standard healthcare practice. During these audits, the checklist can reassess the compliance status of all software systems, ensuring ongoing adherence to HIPAA standards.
After Software Updates or Upgrades
Whenever software is updated or upgraded, reassess it using the checklist. Updates may affect how the software handles PHI, making it necessary to ensure continued compliance.
When Responding to Reported Security Concerns
If there are any concerns or reports regarding the security of patient data, the checklist should be used to conduct a thorough review of the implicated software to identify and rectify any compliance issues.
Training and Onboarding New Staff
Use the checklist as part of the training material for new staff members. It helps them understand the importance of HIPAA compliance in software usage within the healthcare setting.
The HIPAA Compliant Software Checklist is a dynamic tool essential at various stages of software lifecycle management in healthcare. Its regular use ensures that patient data is always protected and compliance with HIPAA regulations is maintained.
What do the Results Mean?
Interpreting the results of the HIPAA-Compliant Software Checklist is critical to understanding the compliance status of your healthcare software systems. The results provide insights into areas of strength and those needing improvement.
Compliant Results
If a software system meets all the criteria on the checklist, it is deemed compliant. This indicates that the software is equipped with robust security measures, respects patient privacy, and adheres to the regulations set forth by HIPAA. Compliant software systems contribute to a secure and trustworthy healthcare environment.
Partial Compliance
In cases where software meets some but not all criteria, it is partially compliant. This suggests that while certain aspects of the software are secure, others require attention. Partial compliance calls for immediate action to address the gaps and ensure full compliance.
Non-Compliant Results
Non-compliance is a serious concern. It indicates that the software fails to meet essential HIPAA requirements, posing a risk to patient data security and potentially leading to legal repercussions. Immediate steps must be taken to upgrade or replace the software with a compliant alternative.
The results from the HIPAA-Compliant Software Checklist clearly show how well your software systems align with HIPAA regulations. Understanding these results is crucial for taking appropriate actions to ensure the security and confidentiality of patient information, thereby upholding the standards of quality and trust in healthcare services.
Research & Evidence
Integrating HIPAA-compliant software in healthcare settings is not just a regulatory requirement but a cornerstone of patient data security. The significance of this compliance is highlighted in various studies and research papers. For instance, Mbonihankuye, Nkunzimana, and Ndagijimana (2019) emphasize the critical role of information technology in healthcare, particularly in data security. Their study underscores the necessity of cloud computing and other data security technologies to preserve patient medical records in a secure environment, as HIPAA mandates.
Another crucial aspect is the compliance of Electronic Health Record (EHR) applications with HIPAA security and privacy requirements. Farhadi, Haddad, and Shahriar delve into this topic, discussing the improved healthcare quality due to EHRs and the challenges in maintaining patient data's confidentiality, integrity, and availability as per HIPAA standards. Their work highlights the need for stringent compliance measures in EHR applications to protect patient data (Farhadi et al., n.d.).
The issue of data breaches in healthcare security systems is another area of concern. Reddy, Elsayed, ElSayed, and Ozer (2021) analyze the reasons behind healthcare data breaches and their impact on patient privacy despite standards like HIPAA. Their findings suggest the need for improvements to current standards to enhance security in the healthcare field.
Furthermore, Choi and Williams (2021) focus on the impact of data breaches in the US healthcare system and the pressure it puts on healthcare providers. They propose a network design that adheres to HIPAA security and privacy requirements, highlighting the importance of a robust compliance audit and risk assessment mitigation approach.
In summary, the research and evidence underline the critical importance of HIPAA compliance in healthcare software. It's about adhering to legal requirements and ensuring the highest security and trust in healthcare services. The studies by Mbonihankuye et al. (2019), Farhadi et al. (n.d.), Reddy et al. (2021), and Choi and Williams (2021) collectively provide a comprehensive understanding of the challenges and solutions in achieving HIPAA compliance in healthcare technology.
References
Choi, Y. B., & Williams, C. E. (2021). A HIPAA Security and Privacy Compliance Audit and Risk Assessment Mitigation Approach. International Journal of Cyber Research and Education.
Farhadi, M., Haddad, H. M., & Shahriar, H. (n.d.). Compliance of Electronic Health Record Applications With HIPAA Security and Privacy Requirements.
Mbonihankuye, S., Nkunzimana, A., & Ndagijimana, A. (2019). Healthcare Data Security Technology: HIPAA Compliance. Wireless Communications and Mobile Computing.
Reddy, J., Elsayed, N., ElSayed, Z., & Ozer, M. (2021). Data Breaches in Healthcare Security Systems.
Commonly asked questions
Carepatron employs advanced security measures, including encryption, secure data storage, and regular compliance audits to ensure all aspects of its platform are HIPAA compliant.
Yes, patients can easily access their health records via Carepatron's secure online patient portal, which provides convenient and confidential access to personal health information.
Absolutely! Carepatron's telehealth platform is designed for secure and efficient virtual healthcare services, offering encrypted video consultations and messaging in compliance with HIPAA standards.




















-template.jpg)